前提
対象OS:NX-OS搭載機器
CML2でいうNexus9000です。
知識:CCNA取得レベル。加えてBGPと再配送を知っていること。
検証環境
CML2.5で行いました。
達成条件
192.168.1.0/24のセグメントに所属しているalpine-1が他のセグメントに所属しているalpine-2(192.168.2.1)やalpine-4(192.168.2.1)に疎通できるようになること。
疎通確認
alpine-1からalpine-3へ
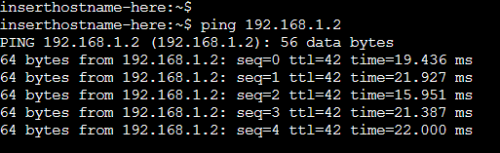
同じセグメントなのでpingは通ります。
alpine-1からalpine-2へ
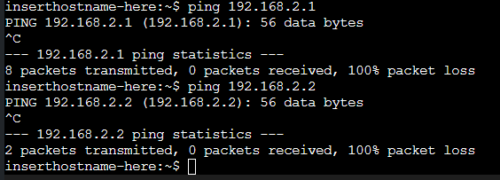
異なるセグメントであり、VRF:AAAに経路情報がないためpingは通りません。
構成図
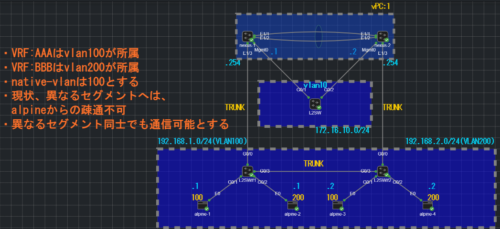
絵だけだと足りない情報を補足します。
・alpine-1と3はDGWとして192.168.1.254を設定
・apline-2と4はDGWとして192.168.2.254を設定
・VRF:仮想的なルーティングテーブルのこと。
事前確認
①show runを取得(※後述しますが、interface vlan100,200にhsrpの設定が抜けてました)
②show ip route vrf allでルーティングテーブルの状態を確認
設定変更
NexusではIOSと異なり、staticによるVRF Routeleakを実施することができません。
そのため、MP-BGPを使用してroute-targetによるタグを利用してRouteleakを実現します。
※どうやら機能的には可能みたいですが、負荷が非常に高くなるため設定できないようにされているようです。おそらく隠しコマンドがあるはず…?余談でした。
設定方法は以下の段取りで行います。
①BGPの起動
route-map ALL permit 10
!
router bgp 65535
vrf AAA
address-family ipv4 unicast
redistribute direct route-map ALL
!
router bgp 65535
vrf BBB
address-family ipv4 unicast
redistribute direct route-map ALL
route-targetはMP-BGPの拡張コミュニティ属性を使用するためBGPを使います。
そのためfeatureコマンドでbgpを有効にする必要があります。
また、BGPのテーブルに載せたルート情報をさらにタグ付けすることでVRF間での経路情報を共有を実現しているため、Routeleakさせたい経路を含むセグメントを一度全てBGPへ再配布する必要があります。
そのため、コマンド例のように ALLという名前のroute-mapを使用してdirect(connected)をBGPに再配布しています。これによってVRF:AAAでいう以下の情報がBGPへ再配布されました。
[再配布された経路(show ip route vrf allより抜粋)]
192.168.1.0/24, ubest/mbest: 1/0, attached
*via 192.168.1.253, Vlan100, [0/0], 00:21:44, direct
②prefix-listの作成
ip prefix-list BBB-to-AAA seq 10 permit 192.168.2.0/24
タグ付けしたいセグメントやIPアドレスはここで指定します。
③route-mapの定義とタグ付け
route-map m-AAA-to-BBB permit 10
match ip address prefix-list AAA-to-BBB
set extcommunity rt 1000:2000
route-map m-BBB-to-AAA permit 20
match ip address prefix-list BBB-to-AAA
set extcommunity rt 2000:1000
タグ付けを行うためのroute-mapを作成します。
match ip address prefix-listコマンドで先ほど作成したprefix-listを選択します。
その後、set extcommunity rtコマンドでタグ付けを行います。
今回は以下のような採番ルールとしました。
・1000→AAA、2000→BBB
・X:Y→Xは配布元のVRF名、Yは配布先のVRF名とする
④エクスポート及びインポートのルートターゲットの作成
address-family ipv4 unicast
export map m-AAA-to-BBB
route-target import 2000:1000
!
vrf context BBB
address-family ipv4 unicast
export map m-BBB-to-AAA
route-target import 1000:2000
export mapコマンドで先ほど作成したroute-mapを指定します。これが、route-target exportコマンド代わりになります。
また、挿入させたいルートのタグを、route-target importコマンドで定義します。
事後確認
①show runを取得(※後述しますが、interface vlan100,200にhsrpの設定が抜けてました)
②show ip route vrf allでルーティングテーブルの状態を確認
③hsrp設定完了後のshow ip route vrf allの出力
hsrpの設定を忘れていたので設定完了後に再度取得したものを載せます
疎通確認
VRF間で無事に目的のセグメントをRouteleakできたので
alpine-1から他のalpineに対して疎通してみましょう。
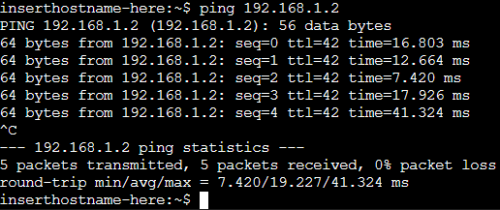
alpine-1からalpine-2へのping(成功)
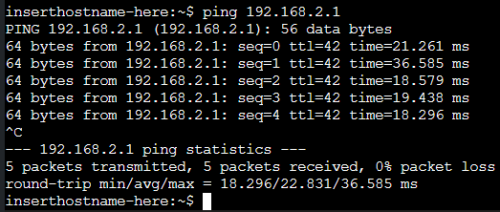
alpine-1からalpine-4へのping(成功)
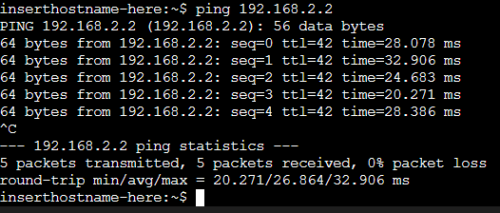
alpine-1からalpine-3へのping(成功) ※元々疎通できます。
まとめ
・VRF Routeleakで異なるVRFの疎通は可能
・特定の経路のみを配布したい場合はroute-mapを使用したタグ付けが必要
・NX-OS搭載機器ではBGPによるVRF Routeleakしか出来ない


コメント